
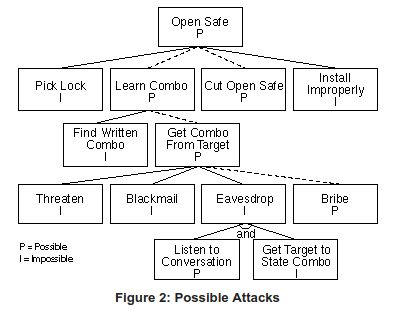
Section 1.3. An Alternative: Attack Trees :: Chapter 1. Threat Modeling and Risk Management :: Secure Linux-based Servers :: Linux systems :: eTutorials.org
GitHub - WouterDep/attacktrees: JavaFX tool for Attack Tree generation and evaluation for CPS systems
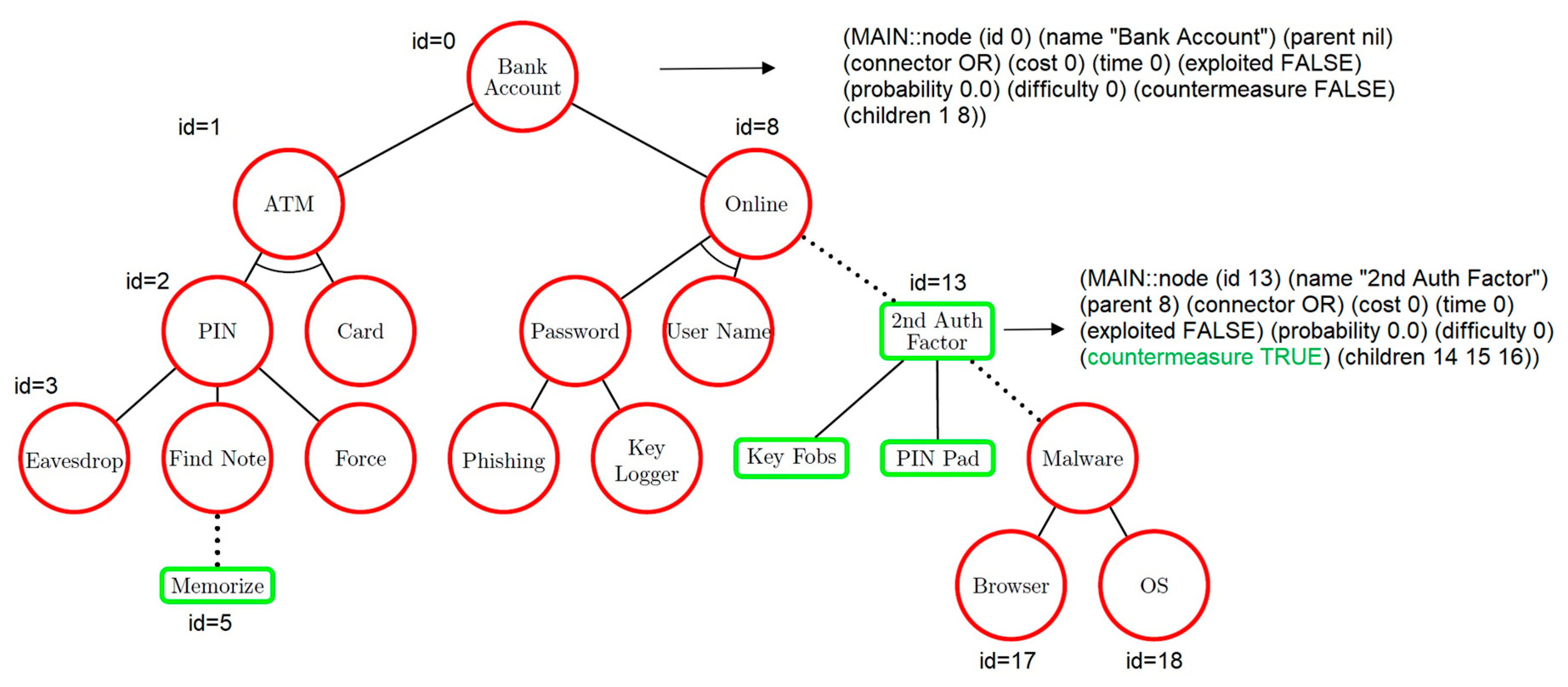
Applied Sciences | Free Full-Text | Method for Attack Tree Data Transformation and Import Into IT Risk Analysis Expert Systems

Section 1.3. An Alternative: Attack Trees :: Chapter 1. Threat Modeling and Risk Management :: Secure Linux-based Servers :: Linux systems :: eTutorials.org





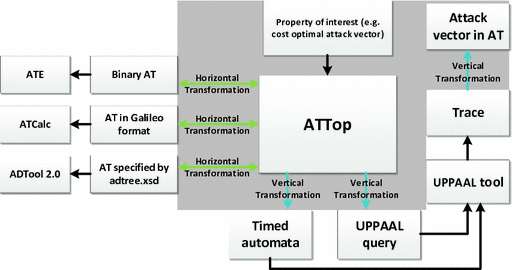
![PDF] Attack-Defense-Trees and other Security Modeling Tools | Semantic Scholar PDF] Attack-Defense-Trees and other Security Modeling Tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3809f354a97c3c67035ec1f8d4c555ba5c5659dd/2-Figure1-1.png)


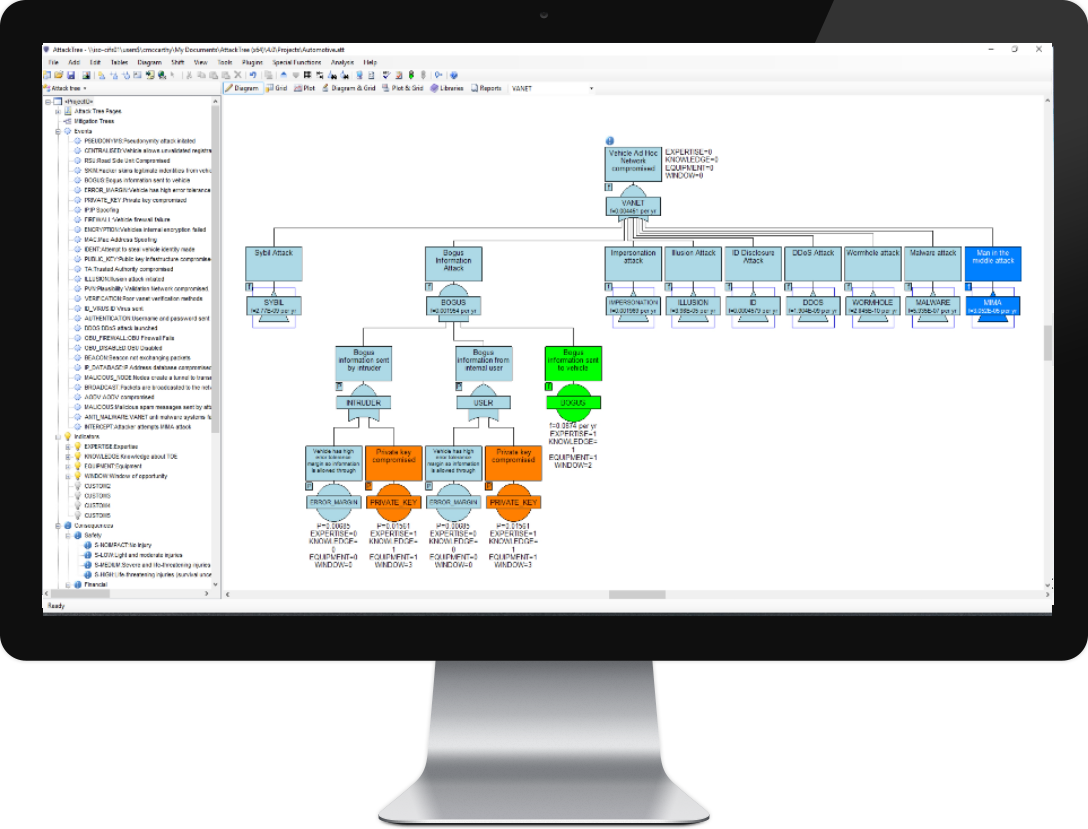



![PDF] On the Meaning and Purpose of Attack Trees | Semantic Scholar PDF] On the Meaning and Purpose of Attack Trees | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/aa9e791e982eec2b042f3f442b6f99e820863ae5/3-Figure1-1.png)
